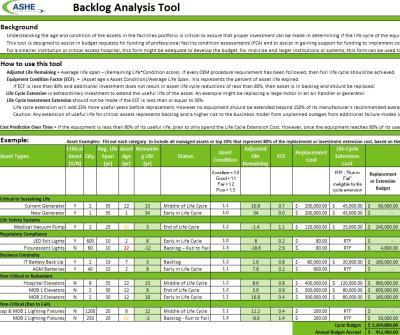
Backlog Analysis Tool
As equipment operates throughout its useful lifecycle, signs of failure will begin to manifest. Neglecting these warning signs can lead to functional failure and ultimately catastrophic failure. Without access to the appropriate resources or a robust asset management program, many health care facilities professionals struggle to escape the vicious cycle known as “reactive maintenance,” wherein a team’s bandwidth to address intentional maintenance activities is lost to backlog of deferred maintenance.
Use this tool to assess the current condition of a system or facility’s asset management program and benchmark the effectiveness of the current investment strategy.
| Download Tool | Members download this tool. Click here to join ASHE! |
| Check out the related HFM magazine article, (coming soon) |
ASHE authorizes the copy, use and customization of this template, by health care facilities for non-commercial use only. In consideration of this authorization, the user agrees that any copy of this document which the user makes shall retain all copyright and other proprietary notices that may be contained therein. ASHE accepts no responsibility or liability for the accuracy or the completeness of the information in this document.

